How to Protect Company Data from Hackers and Employees
June 2, 2023
88% of organizations have experienced cyber attacks or data breaches in the past year (according to computer security analysts). This growth is due to the introduction of popular technologies with a low level of protection and a weak level of cybersecurity literacy of customers.
On average, only 5% of companies' folders are properly protected (according to Varonis). Of course, the losses from such attacks can be great. In 2020, the losses of companies totaled about $1 trillion. Loss of personal data may result in the personal liability of the application owner. But the loss of corporate information or the leakage of trade secrets can destroy a company altogether.

In this article, we are not talking about a security threat when special devices are used to intercept network traffic or remotely scan monitors. We're talking about the necessary minimum data protection that every company can provide.
There are many information leakage channels in any company: messengers (Skype, Telegram, Slack), email, cloud storage of files, social networks, digital and even paper media. Using all these tools, you need to understand that they can become the subject of interest of attackers or even competitors. In this article, we'll show you how to protect customers' and business data from hackers and employees.
How to protect company data from hackers
Based on our experience in ensuring data security, we have defined internal safeguards to protect company information from hackers. We use these methods when developing security and data protection software.
We divide all data protection methods into two main ones: technical and organizational. Each of them is implemented using different tools.
Technical Methods
We defined technical methods of company information protection:
1.Implementation of special software products.
They protect data from copying or complete deletion, from losing passwords or keys. They also block virus threats and phishing attacks on the company’s internal servers or cloud spaces.
We have extensive experience in developing data protection software. The software developed by us ensures data security and confidentiality. It also reduces the risks of significant financial losses for our clients.
2. Checking program code for vulnerabilities
There are services that determine the vulnerability to external hacker attacks on your site, application or internal system. The overall threat level is calculated and the vulnerabilities that need to be fixed are indicated.
We recommend using CyberGuard. It’s the only service that collects vulnerabilities not only in program code but also from the operating system itself.
3. Regular backups.
At least with the duplication of all important corporate data. For example, on physical media and an internal server of the company with hardware protection.
4. Duplication of subsystems and networks in their most important segments.
5. Internal company-owned VPN.
6. Availability of firewalls and security systems at the level of corporate routers.
7. Availability of backup batteries for computers and internal servers of the company.
8. Complete prohibition of the use of unlicensed software, as well as applications downloaded from unknown or unofficial sources.
Ideally, critical objects of the enterprise information infrastructure should be supported by software that has appropriate security certificates.
9. Use two-factor authentication wherever possible
10. Use only special software for generating, applying and transmitting passwords.
Sometimes companies do not employ a separate information security specialist. Then the way out may be to invite a certified auditor from an external company. They will be able to audit the IT infrastructure and give recommendations. We, as developers, can implement them and protect customers’ and business data from external and internal threats.
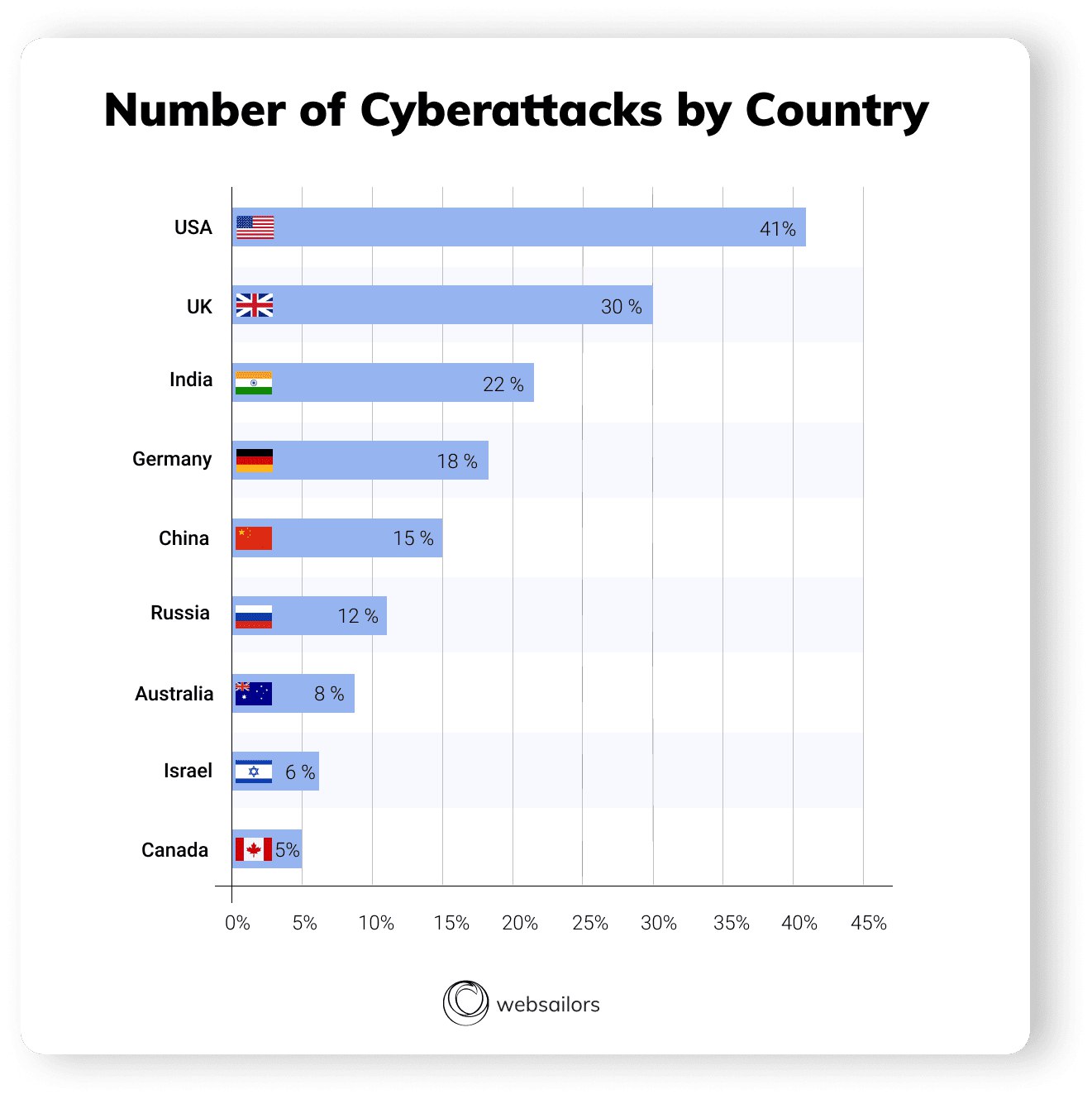
Organizational methods
Organizational methods of defense against attacks are based on corporate “information security regulations”. This is an internal document that takes into account the company’s business processes and its information infrastructure.
As the main organizational methods, we recommend:
1. Internal documentation of the company, which establishes the rules for working with software.
- Regulate password protection of a high degree of reliability for all systems.
- Use hardware (tokens) and electronic digital signatures.
- Regulate access rights only after the conclusion of the relevant agreements
- Use only secure corporate accounts in all necessary services.
2. Briefing on safety precautions and rules for the use of technical means.
3. Delineation of areas of responsibility of employees.
This is necessary to eliminate the likelihood of losing large datasets of one employee. And also to exclude the distribution of important documents, or prevent critical changes in the codebase.
4. Access system and regulated access to the premises of the company. Keeping an automated record of the conditions of being at the workplace.
Any access to the company’s information space should be provided only after passing through the authentication and identification procedures. We clearly distinguish between these two concepts. Authentication is checking the concurrence of the user parameters and the parameters stored in the system. Identification is the procedure for assigning unique user parameters in the system to the actual user.
We recommend that you implement access to most resources after going through three stages:
- Access to the building with a personal hardware key.
- Passing control at the security perimeter.
- Authorization in the information space using additional password protection and/or two-factor authentication.
5. Creation of a fire safety, security, alarm system, a network of emergency sensors and constant video recording of premises.
6. Use only proven means of electronic communication with a high degree of protection and encryption of correspondence.
Use exclusively corporate mailboxes for work. In addition, it is recommended to constantly monitor the research of companies that evaluate the systems used.
7. Destroy any unnecessary paper media using special devices.
8. Use only corporate mobile devices for developing and testing applications (if this is your specialty)
9. Sort your trash and control waste paper.
10. Assign a degree of confidentiality to each data group:
- The highest degree of secrecy.
- Strictly confidential information.
- Confidential information.
- Information with limited access.
- Open data
Such ranking helps to better organize the access system, minimize the risks of data leakage and improve protection from hackers.
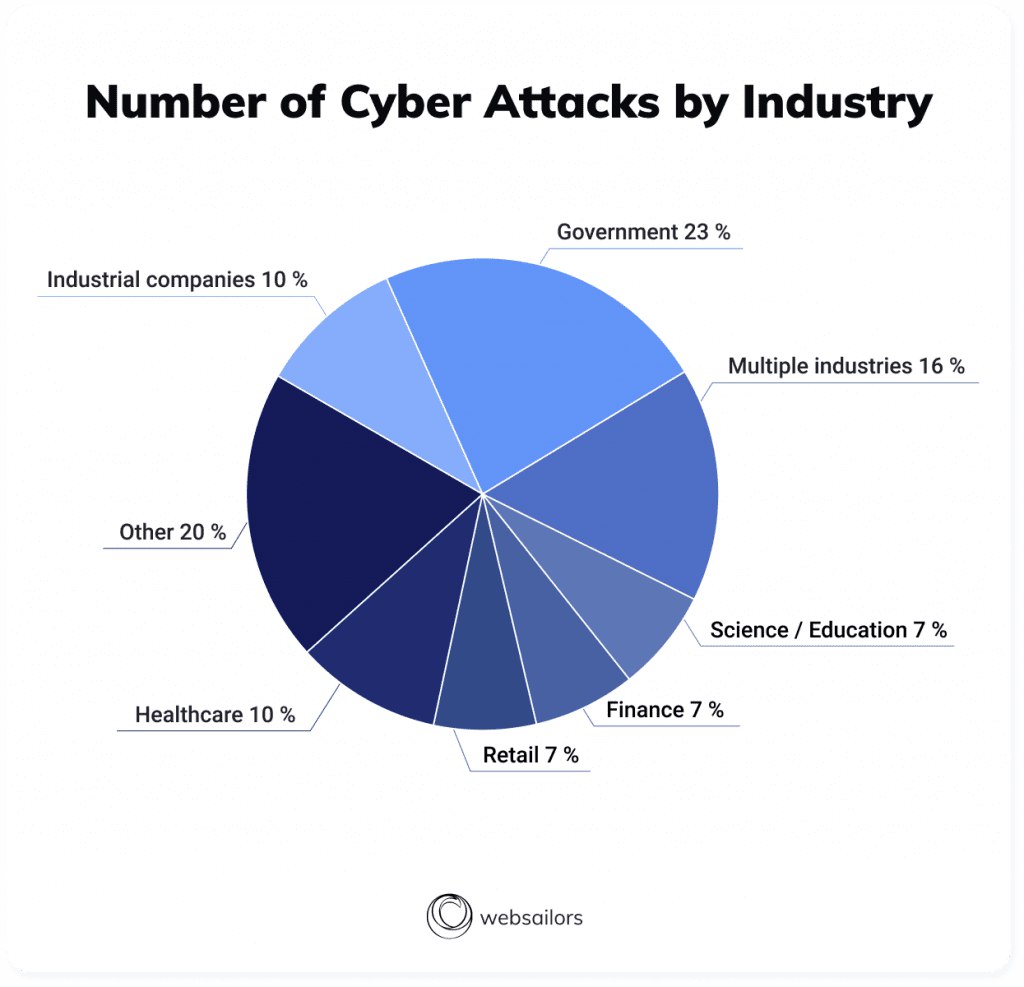
How to protect company data from employees
Another problem can be unscrupulous employees of the company itself. 95% of cybersecurity breaches are caused by human error (according to Cybint). We can advise on how to recognize a situation when destructive work is carried out within the company.
Firstly, if customers abruptly leave the company, it is most likely that the customer base has leaked. It is also possible that someone deliberately spoils the relationship with clients or takes them away, preferring to work with them directly.
Second, there are dramatic changes in the behavior of some employees. For example, improved financial situation, decreased interest in work, increased correspondence on the Internet, frequent sending of password-protected files, access to external resources via VPN.
Third, there is a constant drain of staff to the same companies. Here, most likely, it’s the work of the “internal” intelligence of another company. Some person monitors your personnel, trains them at the expense of your company and then lures them “to himself”.
The fight against such a human factor is difficult but real. We advise:
- Offer competently executed contracts with employees providing compensation for losses for such activities.
- Motivate and involve employees in the corporate life of the company.
- Maintain a competitive level of wages.
- Conduct training on corporate security and improve the qualifications of employees in this area.
- Use special tools to monitor the work of employees, including registrations of programs used, visited sites, open browser tabs, and so on.
- Use workplace safety auditing and special technical means to detect suspicious traffic. For example, DLP systems (Data Leak Prevention). They allow you to track the transfer and printing of files, sudden bursts of Internet communication, visits to sites that are not typical for work, etc. It also conducts a linguistic analysis of correspondence and documents and identifies the danger of a leak using keywords.
Real customer story
Our client’s database was hacked and the data was encrypted. The hackers left a message demanding a ransom fee with bitcoins to their wallet and only after that they will return the data.
Fortunately, the database was empty (test data only). But this made our client think and conduct a system security audit. Our development team implemented all audit conclusions in a short time.
The types of work that we have performed to protect company data from hackers:
- set up a firewall on the server,
- closed routes with access rights,
- encrypted individual tables with user data in the database,
- used https,
- closed swagger from external requests on the server and opened it if everything is running on the developer’s machine,
- used cross-site scripting protection,
- split the database into a separate server under the control and protection of the hosting company.
Summary
We have compiled for you some internal safeguards that will help you avoid large financial losses. Summarizing the above, we must note that data protection is an extremely important process that can affect the future of the company.
If you need a software development team with expertise in creating data protection system email us at contact@websailors.pro
WebSailors Ascends to the Top of the Software Development Industry: Recognized as a Top Company by Techreviewer.co
How to optimize your website or mobile app for search engines
GoodFirms has interviewed WebSailors’ CEO, Denis Benyaminov
Do you have any questions? Let’s discuss your project
Contact Form

